#1 Malware Guide in 2022
Malware is a terrible force. Each year, unsuspecting victims lose millions of dollars and have their identities and private data stolen. Businesses lose data and revenue, and governments fall prey to corrupt hackers — these are some of the reasons why you must take precautions.
This article aims to help you better understand what malware is and how you can protect yourself, your family, and your business from its damaging effects.
What is malware?
Malware is a catch-all term that encompasses all forms of harmful software.
Often confused with “virus”, in reality, the terms are not synonymous — a virus is only one form of malware. Malware comes in many forms — including spyware, worms, trojans, and ransomware — and may infect your device in several ways. Most often, infection occurs via malicious links or infected files downloaded from the Internet.
The damage this malicious software can do varies. From filling your screen with intrusive pop-up ads to encrypting essential files and demanding a ransom in return — the threats are endless. Although hackers often use malware to infect computers for financial benefit, malware can also be used to test security systems for weak points, spying. It can even be used for political gain.
There’s a good chance that the computers you’ve used in the past had a malware infection at some point. Traditionally, Windows has been the most common malware target, with macOS and Android trailing close behind. A rule of thumb: as a device increases in popularity, so too will the number of malware attacks.
Most often, malware infection occurs via malicious links or infected files downloaded from the Internet.
How can malware infect my device?
Malware can spread to your device via:
Email: Cybercriminals send out millions of phishing emails laced with malware daily. Although these emails will usually end up in your spam folder, the occasional one will make it to your inbox. Granted, the list of email scams is endless; most of them contain malicious links or attachments or requests to send money.
Text messages: Messages that contain suspicious links via SMS or instant messaging apps are also common. These messages can be especially effective if they’re sent by people you know. In this case, a type of malware was most likely used to hijack the email accounts of your friends and associates.
Websites: If you click on a malicious link, you may end up on a website infected with malware. There are several ways your computer can become infected with malware from a website. Common methods include clicking on malware-infected ads or not clicking at all (drive-by download).
Operating system: Cybercriminals can exploit an operating system’s vulnerabilities as well. They do that as quickly as possible to avoid software patches designed to correct existing vulnerabilities. That’s why it’s essential to update your operating system and programs as soon as an update is available.
Computer programs: It’s no wonder that software programs often contain malware. In some cases, a program itself can be malware (a trojan), or it can transmit malware to your system. In short, a talented hacker can exploit any vulnerability that a program may have.
Apps: Mobile apps both frequently contain malware or are malware themselves. These malicious apps can pose as legitimate apps and even imitate popular apps like Facebook or Twitter. Many apps also contain adware that quickly leads to annoying pop-ups or non-consensual malware installation.
Flash drives: Although the technique of using USB sticks to spread malware is not as popular as it used to be, you should still be aware of it. Always do your best never to connect a flash drive that you’re unfamiliar with to your computer; however, if you do, make sure your computer has a strong antivirus program, such as Bitdefender or McAfee installed.
Here’s an intuitive way of explaining how malware from a phishing email can infect your PC:
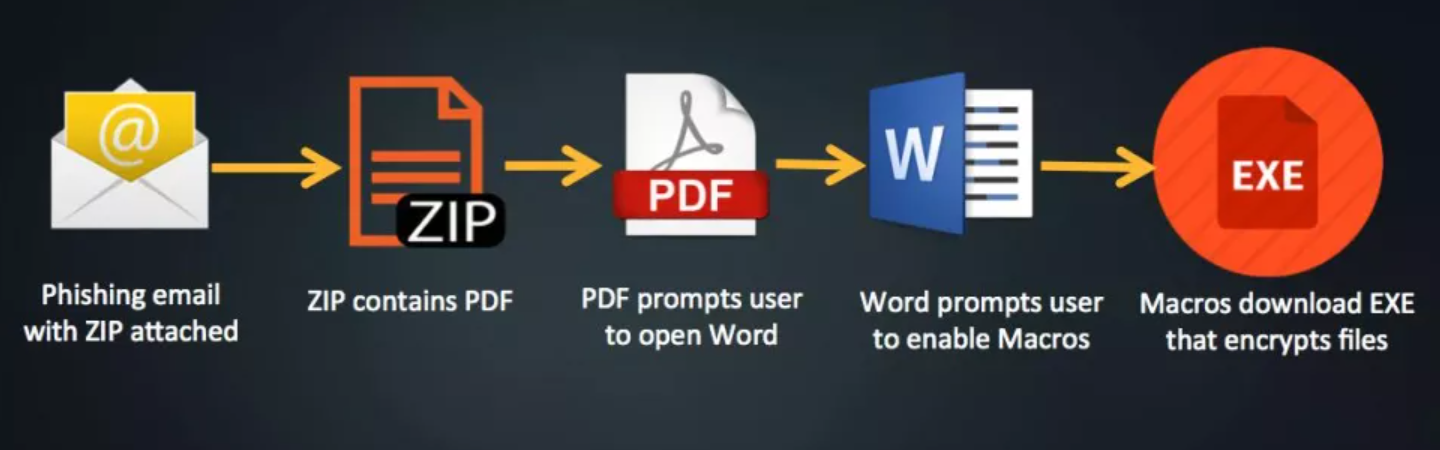
Source: ITProPortal
Malicious apps pose as legitimate and even imitate popular apps like Facebook or Twitter.
Types of malware
Here’s a list of the most common forms of malware. Note that each name is an umbrella term consisting of multiple forms of malware.
Spyware
Spyware is a form of malware that secretly downloads to your computer to spy on you. It records your keystrokes, clicks, usernames and passwords, credit card details, and more. Typically, you don’t know your system is infected with spyware until you notice some suspicious activity with your online accounts.
Spyware secretly records your keystrokes, clicks, usernames and passwords, credit card numbers, and more.
Trojan
Trojans disguise themselves as legit programs and other files. Once you install them, they’ll unleash a full-scale attack on your system, creating and opening up a backdoor for other forms of malware to get in. Thus, trojans are responsible for all sorts of destruction, including data theft, deleting and encrypting files, monitoring your internet usage, and more.
Adware
Adware is unwanted software that typically hijacks your web browser. It blasts your system with popup ads, manipulates your homepage and default search engine, and can even monitor your computer activity. Adware attackers illicitly make money by feeding you ads that often contain malware like keyloggers or ransomware.
Ransomware
Ransomware is malware that encrypts your files or locks you out of your device. Once this has been accomplished, a ransom will be demanded in the form of cryptocurrency — this makes it hard to trace. Ransomware is common as it can be easily purchased on criminal marketplaces.
Viruses
A virus is the most traditional strain of malware. Like its biological counterpart, a virus attaches itself to another program and unleashes a dangerous payload that corrupts files and can render a system’s functionality completely useless. As its name suggests, a virus spreads to another program or computer through a network only if a user opens the software that contains the virus.
Worms
Like viruses, worms are malicious pieces of code that can damage systems and spread to others via a network. In order to spread, they usually exploit a vulnerability in an infected machine or come attached to a seemingly harmless program. Unlike a virus, worms don’t require a user’s actions.
Rootkit
Rootkit consists of a group of malware that, once it infects a device, enables an attacker to access said device remotely. A rootkit can hide exceptionally well in your system and allows other malware to hide in plain sight by disguising it as essential files.
Keylogger
Keyloggers are software programs that record your keyboard strokes. This software is especially dangerous if you tend to log into your banking accounts or other sensitive material on your computer or mobile phone. Some corporations even use these tools to spy on their employees.
Cryptominer
Also known as a cryptojacker, cybercriminals use this form of malware to mine cryptocurrency via a computer’s processing power. If it gets on your system, you’ll notice an increase in usage of your CPU and video card (they’ll get hotter and louder).
Fileless malware
Fileless malware uses an operating system’s files and services to control devices and networks using exploits or scripts. As it doesn’t leave a concrete trail behind, fileless malware can be difficult to control and remove. An up-to-date anti-malware suite can help you keep fileless malware at bay.
Malware file types
If you’re wondering what kinds of files can infect your computer, Check Point Research offers insights via their annual cybersecurity report. Online, the most common infected type of file you can download is .exe, and the common type of file transmitted via email is .doc. So, beware of these kinds of files and use a solid antivirus to detect malware before it can infect your PC.
Source: Cyber Security Report 2021 by Check Point Research
Malware statistics
To help you understand how harmful malware is, we’ve compiled a list of malware statistics from different sources on the web. Here’s what you need to know.
The reputable AV-TEST Institute discovers over 350,000 new forms of malware and potentially unwanted applications (PUAs) daily. Also known as zero-day attacks, these new threats can wreck computers that lack a good anti-malware solution.
Furthermore, AV-TEST detected over 1.1 billion forms of malware in 2020. This number has been on the rise for years, as seen in the chart below.
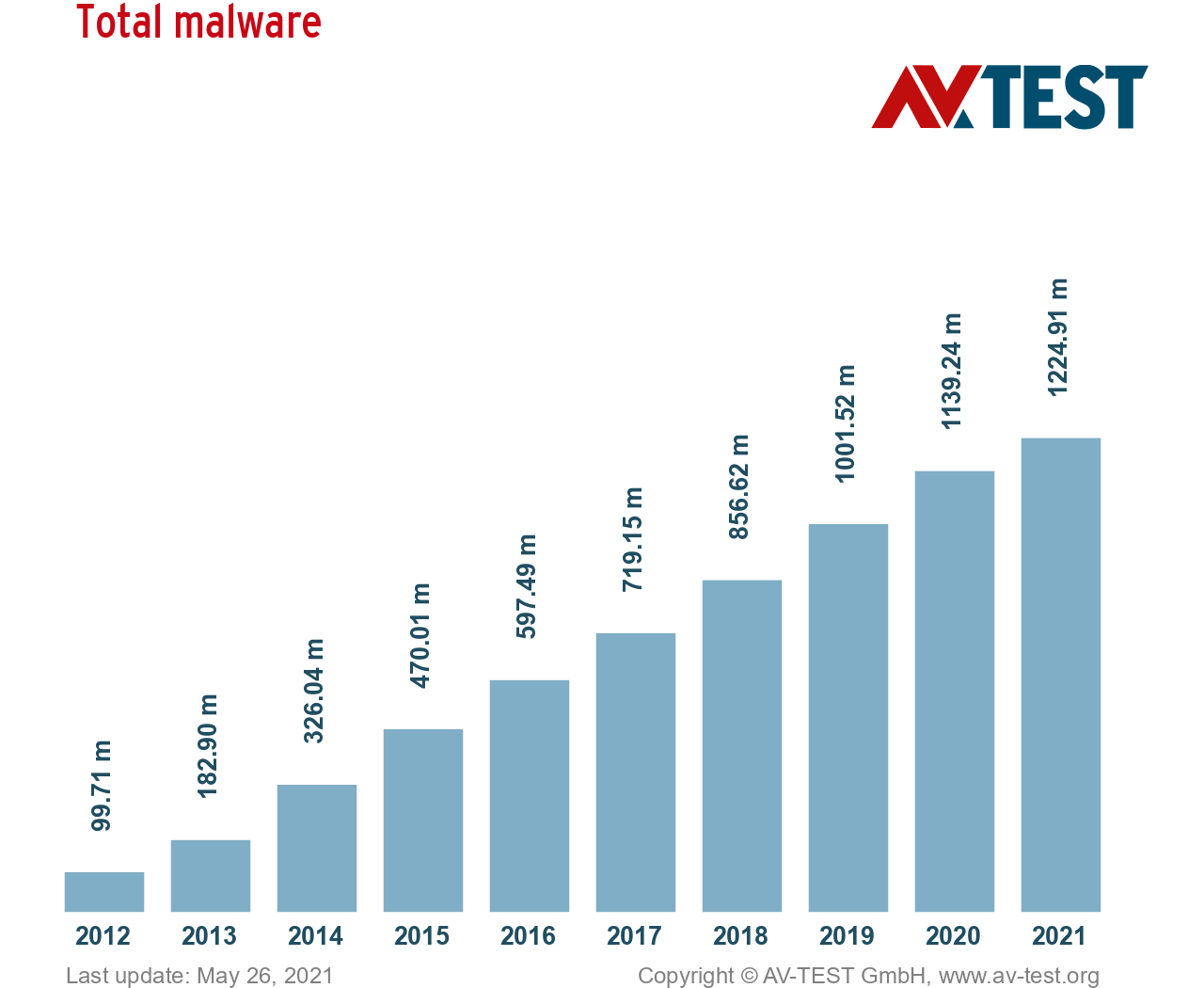
Source: AV-TEST
That’s not all. Every day, Google’s Safe Browsing finds thousands of new unsafe sites. This goes to show that the web is full of hidden dangers, including phishing websites. From the following report, you can see that although the number of malware sites has decreased in recent years, the number of phishing sites has increased dramatically.
Here’s another interesting fact: according to Statista, the number of new forms of malware worldwide has increased by over 100 million from 2019 to 2020.
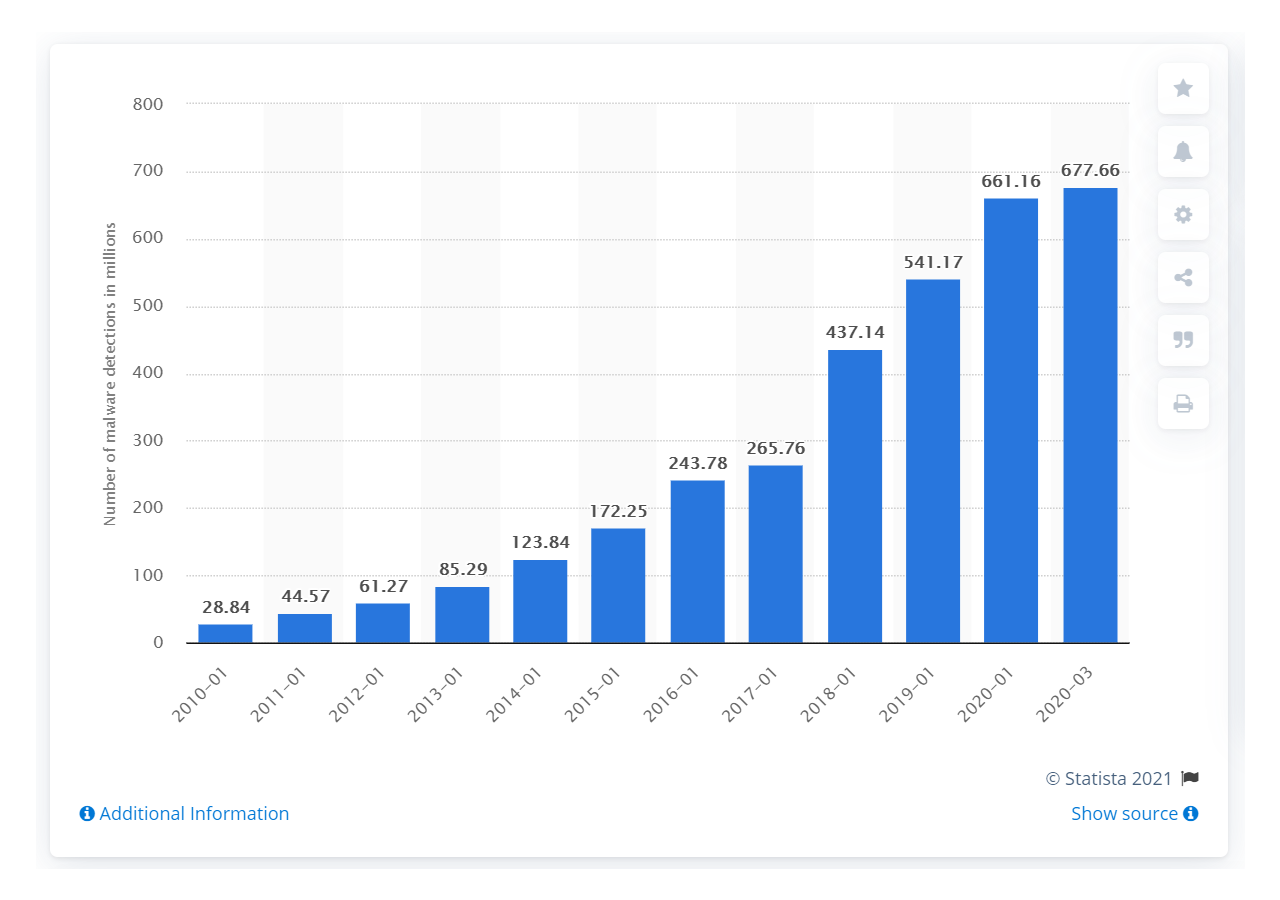
Source: Statista
Although the number of malware detections has grown year by year, in 2020, they decreased in comparison to the previous year. Still, the number is in the billions.
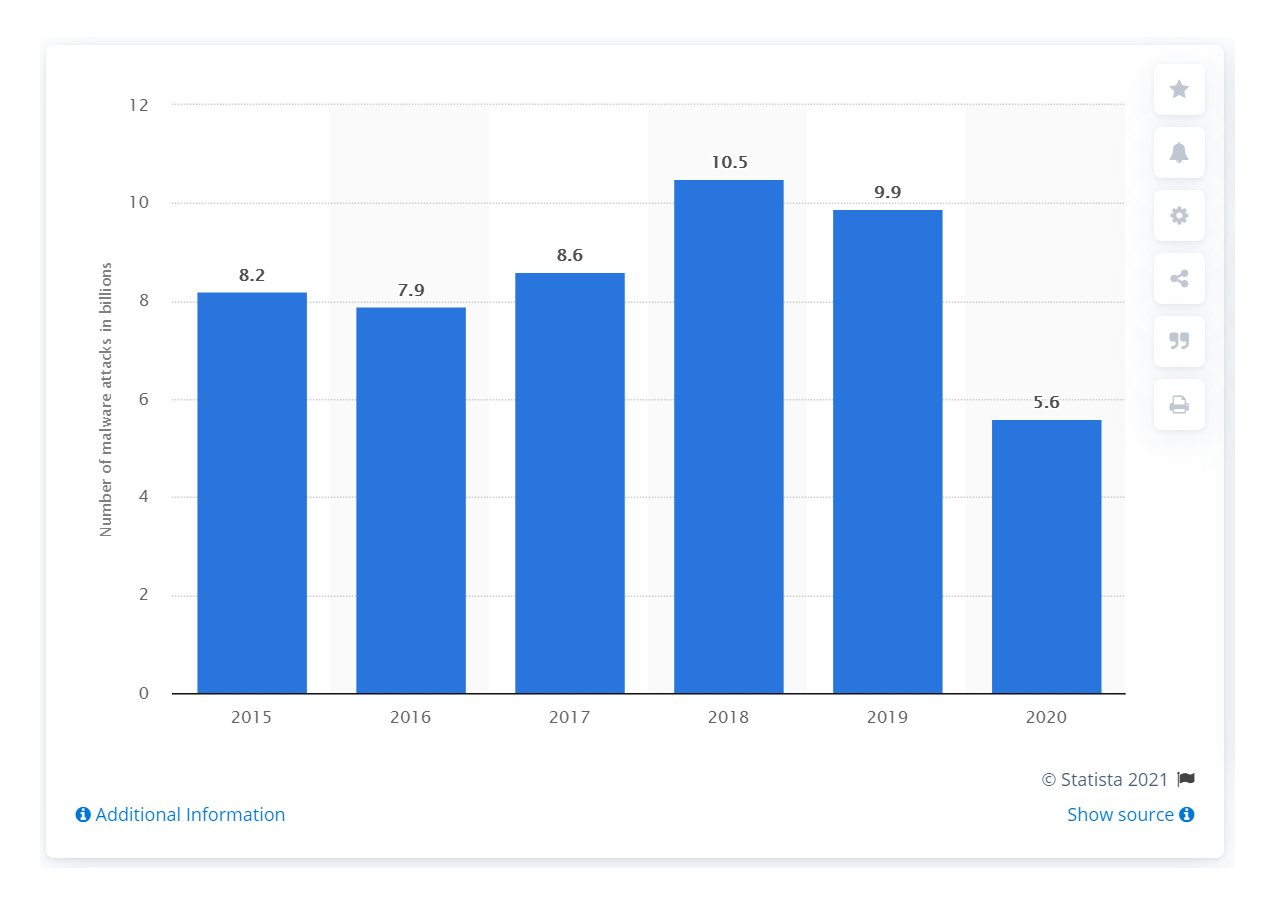
Source: Statista
Malware on Android
Android has long been a target of malware. Much like computer malware, the malware that affects Android can do all kinds of damage. This is because the malware that affects Android is diverse, including trojans, adware, spyware, ransomware, and more.
An Android device may contract malware in several ways, including by downloading fake apps from unofficial app marketplaces and even from the official Google Play store. Clicking on dubious links or malicious pop-ups is also a surefire way to infect an Android device with malware.
Here’s a concerning fact: the number of new mobile malware (most of which is Android-based) that McAfee detected in 2020 increased drastically. That goes to show that the Covid-19 pandemic was productive for mobile hackers.
Source: McAfee Labs Threats Report
Malware on iPhone
Although iPhone malware is very rare compared to Android malware, iPhones aren’t immune to malware. iPhone users can still get trojans, spyware, adware, and other forms of unwanted software if they don't exercise vigilance.
iPhone users can still get trojans, spyware, adware, and other forms of unwanted software.
Cybercriminals typically send scam messages and emails during holidays or in times of crisis. VIPs are also frequent targets of iPhone phishing attempts, with many CEOs having been successfully fooled.
Note: jailbreaking your iPhone or downloading apps from unofficial sources increases the chance that your iPhone will be infected with malware.
Mac malware
Although most malware detections occur on Windows, more and more Macs have become malware targets due to their increase in popularity. For this reason, even Mac users should consider a dedicated Mac malware removal program like Norton or McAfee.
Malware attacks Macs through phishing attacks or via the user visiting suspicious websites. According to Malwarebytes, adware and potentially unwanted applications (PUAs) are the most common forms of malware that affect Macs. These forms aren’t always malicious, but they can open the door to more harmful types of malware.
Moreover, according to AV-Test, MacOS malware has drastically increased in 2020 but decreased by a lot as of May 2021.
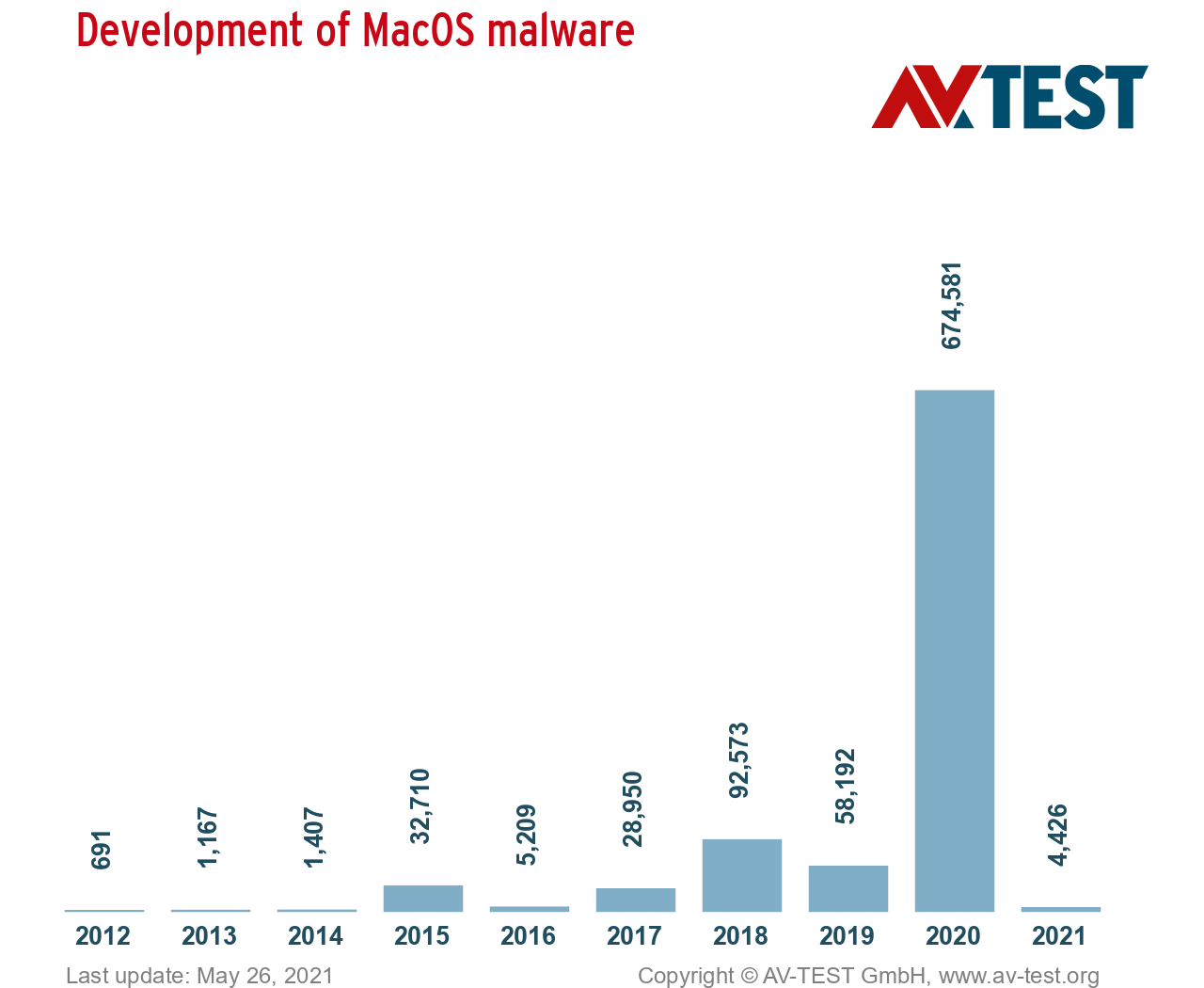
Source: AV-TEST
How to keep your devices safe from malware
If you remain vigilant and follow the steps below, you can protect your device from most varieties of malware:
Only visit websites you know are safe. Be suspicious of any links from emails, text messages, websites, apps, programs, or your browser. Pay attention to a link’s domain name — unusually spelled websites may be risky. Use a robust antivirus to filter out good links from bad ones on the web.
Never click on pop-up ads. If you’ve disabled pop-up ads in your browser, good for you! However, if pop-ups still appear, do not click on them. Your device could have adware. Use an anti-malware program to resolve this issue.
Don’t open unsolicited email attachments. There are plenty of phishing attempts on the internet — your email provider thwarts most of them. If you spot a suspicious email, don’t click on any links or download any files located in it. Remember that many phishing emails attempt to imitate well-known brands.
Don’t access dubious websites. To prevent a malware invasion on your device, avoid visiting untrustworthy websites, such as peer-to-peer file-sharing networks, illegal movie streaming sites, or even adult sites.
Keep your software up-to-date. Regularly patch and update any installed programs, apps, and operating system on your device. Cybercriminals often take advantage of vulnerable software, injecting it with malware; a software update will fix that!
On mobile devices, only download apps from official app stores. Whether you use Android or iPhone, avoid downloading apps from suspicious sources as they often host malware. Even if you download apps from official marketplaces, be sure to read over any customer reviews carefully. Be aware — some apps are fake, specifically designed to inject spyware on a victim’s phone.
Businesses should create mobile security policies within their organization. Considering the numerous devices and operating systems that employees use at work, it’s essential to create a strong barrier against online threats and social engineering.
Get a reliable antivirus solution. It’s easier to stop a threat than to deal with the damage it has caused. An antivirus solution can stop malware in its tracks before it can damage your system or steal your personal data. Your anti-malware utility should include a robust set of features. For example, it must be able to quarantine detected threats, protect your online privacy, update its virus database, scan your device in real-time, and more.
Pay attention to a link’s domain name — unusually spelled websites may be risky.
How do you remove malware?
If you lack a legit malware removal program, get one right now! These tools feature better scanning and removal capabilities than the default antivirus tools found on Windows (Defender) or macOS (XProtect). They can also detect and eliminate most threats, which lowers the risk of losing files or having to erase your disk and reinstall your OS.
FAQs
Is malware a virus?
Malware is a term that refers to multiple software threats, not just viruses. A virus is a type of malware that requires the user to open it in order for it to spread. Once it has unleashed its payload (deleting or altering data), it spreads into other programs and computers through networks.
Get a reputable antivirus program like Norton to keep viruses and other malware at bay.
How does malware work?
How malware affects a device depends on what kind of malware it is. For example, worms enter systems via a downloaded file or network connection. As a result, it can change the way a computer or network operates. A trojan looks like a legit program or file but can create backdoors for other forms of malware, steal data, or even help launch a DDoS attack.
No matter the type of malware, a strong anti-malware solution will protect your sensitive data.
What are some examples of malware?
Malware, which stands for malicious software, comes in many different forms. Malware variants include viruses, worms, trojans, rootkits, ransomware, exploits, and more. Each of these digital threats has unique capabilities, from erasing your files to hijacking your camera. Steer clear of these damaging pieces of code by installing a full-fledged antivirus program (Norton is one of them).
How do I get rid of malware?
You can get rid of malware by installing a cybersecurity software suite. Each of these advanced tools includes a malware scanner and can even detect and quarantine malware at your discretion. In addition, these cybersecurity suites will protect your device should you come across dangerous websites, files, or emails.
Who creates malware?
People create malware for various reasons — mainly for illegal purposes, such as stealing sensitive data to gain money, spying on someone, attacking a political group, sabotaging, and hacktivism. Those who create malware either use it themselves or sell it on the dark web. Having a trusted antivirus software can significantly increase your device’s defenses against malware.
Octav Fedor (Cybersecurity Editor)
Octav is a cybersecurity researcher and writer at AntivirusGuide. When he’s not publishing his honest opinions about security software online, he likes to learn about programming, watch astronomy documentaries, and participate in general knowledge competitions.