#1 Phishing Guide in 2022
Did you know that a new phishing website is launched every minute? But phishing attackers don’t just use websites to fool their victims. All sorts of methods are used, including SMS, email, social media, and more. No one is safe. Even high-ranking officials can fall victim. In the following article, you’ll learn what phishing is, how it can harm you, and how you can protect yourself and your loved ones from its reach.
What is phishing?
Phishing is a type of fraud where the attacker poses as a reputable organization or person.
The aim is to trick the victim into sharing sensitive information like passwords and credit card information or to convince the target under false pretenses to send money or install software containing malware. Phishing affects hundreds of thousands of people and businesses worldwide and is one of the most common forms of cybercrime.
Similar to the sport of fishing, cyber phishing criminals lure their victims into a trap. This type of attack is mostly carried out through email, but cybercriminals have also been known to use SMS texting, instant messaging, and voice calling to lure their victims. In fact, no operating system is truly safe from phishing — Windows, Mac, Android, or iPhone users can become victims of this type of fraud.
Even though phishing is a technologically simple form of cyberattack, it’s still highly effective and dangerous; it’s much easier to trick someone than to penetrate a computer’s defenses. Attackers send millions of fraudulent emails every day, hoping that someone will eventually take the bait.
Source: APWG’s Phishing Activity Trends Report
A typical example of phishing is when a user receives a fraudulent email containing a corrupt link from what looks like a trusted email from a familiar company. The attacker provides the user with a reasonable explanation for clicking on the link (the bait). Once the target has clicked on the link, malware is downloaded (and sometimes installed) onto the user’s device. Often, that malware is actually spyware that’s designed to steal a user’s data.
According to the FBI’s 2020 Internet Crime Report, the Internet Crime Complaint Center (IC3) received 791,790 complaints from American civilians and businesses in 2020 — a 69% increase from 2019. In addition, IC3 recorded more than $4.1 billion in losses in 2020. That’s a big jump from the $3.4 billion recorded in 2019. Of all of the reported incidents, phishing and similar scams were the most common.
Source: FBI’s 2020 Internet Crime Report
...phishing affects hundreds of thousands of people and businesses worldwide each year.
Remember, the attacker wants you to:
Fortunately, you can avoid phishing attacks once you know the warning signs.
How to recognize phishing
Most phishing attacks follow the same pattern, making them easier to detect for those who remain vigilant. Here’s how you can recognize phishing scams:
It imitates a well-known brand. Attackers often send fraudulent emails that impersonate famous brands, such as Apple, Amazon, or reputable banking services, to convince their victims that emails are genuine. Did you know that, according to Check Point, Apple was the most imitated brand used for attempted phishing attacks at the beginning of 2020? In the second quarter, however, Google and Amazon phishing emails were more prevalent.
Phishing attackers replicate real companies’ logos and brand features to make their emails extra hard to spot. Attackers also use a technique called “spoofing” to lure unsuspecting targets. Spoofing is achieved by copying an actual sender’s display name, email address, and domain name. Although hackers can mimic a company’s email address, they can never use an official address.
The sender is unfamiliar. If the sender is someone you don’t recognize, you should be suspicious. Consider deleting the email, or, if you want to read it, just don’t click on any links or attachments.
The sender is familiar, but the message looks fishy. Other times, you may recognize the sender, but it’s not someone you usually talk to. If this is the case, then that person’s email or instant messaging account may have been breached, and an attacker is using it to send you messages laced with malware.
They use a generic greeting. Most scam emails will not be addressed to you specifically. Often, they are sent to thousands of people, in which case, the attacker probably doesn’t know your name. Instead, these emails will contain phrases such as “Dear Sir or Madam” or “Dear Customer”.
It’s littered with grammar mistakes. Phishing emails often contain obvious grammatical and spelling errors. Formatting, design, and image placement may also appear to be clumsy.
There’s a sense of urgency. Marketers often use a few tactics to entice their target audience to take the desired action quickly. Cybercrooks also use these tactics, but in a malicious way. For example, they may claim that your account will be suspended if you don’t change your banking credentials immediately (using a link provided in an email). Other times, a message may encourage you to send money to a relative that is experiencing a problem.
The offer is too good to be true. Sometimes, phishers will claim that you’ve won something very attractive, such as a new laptop or an exotic trip — these are classic scams. Don’t be deceived by them, even if they look irresistible.
The links or attachments are suspicious. Almost all phishing messages contain a malicious link, attachment, or both. Some of these links may appear to be genuine at first glance, but upon closer inspection, they’ll look suspicious. Simply hover over a link to inspect it, but whatever you do, never click on it! Watch out for subtle misspellings (such as “Anerica” instead of “America”). Also, don’t download any attachments if you’re not sure that they’re safe.
Attackers often send fraudulent emails that impersonate famous brands, such as Apple.
Types of phishing attacks
Phishing scams have evolved and grown in numbers over the years. The methods presented below are so efficient that they’ve lasted for decades.
Bulk email scams
Most phishing emails are sent to millions of users across the globe. Although they don’t usually target a specific person, sometimes victims are selected based on the services they use. Example: groups of people that use the same bank, social media, or other accounts.
Keep in mind, the messaging contained in phishing emails varies. For instance, an email may ask you to:
Click on a link to update your payment to a website
Download a program that promises to speed up your computer
Send money to a friend that has suffered an accident
Most phishing emails are sent to millions of users across the globe.
Clone phishing
Clone phishing might be the most difficult scam to detect. That’s because the attackers send nearly identical versions of an email with which a victim is familiar. For example, an email that notifies you about paying your next Netflix bill.
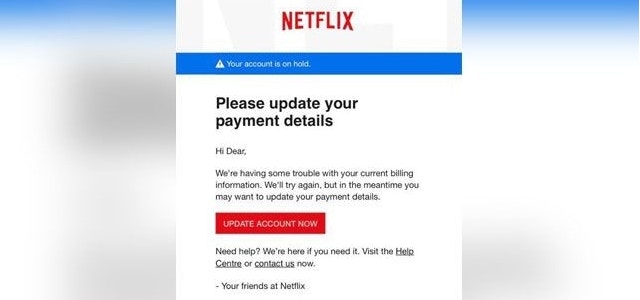
Source: FTC.gov
The scammers use the same body (header, fonts, colors, design, language, etc.), but change the link to a malicious one. The exact email address of the sender will not be the same, either. Only the official sender can use the real address.
Spear phishing
This form of phishing is the opposite of mass-scale phishing in that spear-phishing targets a specific person or organization. Often, the message is explicitly written for the target victim. Thus, attackers first research their victims to uncover names, job titles, colleagues, and other private details.
An example of spear phishing is when an attacker poses as the boss of a company or as someone who handles payroll. The phisher may direct an employee to send money to a vendor using a fraudulent link. Using urgency and specific information, the scammer dupes the employee into handing their money over.
Whaling
Similar to spear phishing, whaling also targets a specific individual or business. The difference is that whaling focuses on big targets, such as CEOs, wealthy people, celebrities, or politicians. Since the victims consist of high-value targets, the data they disclose is highly sensitive. Attackers spend countless hours researching their targets and creating elaborate emails to con their victims successfully.
Even though the targets of whaling are important people, many of them fall prey to these attacks. For instance, John Podesta, Hillary Clinton’s campaign chairman, was duped into providing his Gmail password to scammers, leading to the Clinton email scandal in 2016. Another famous example of whaling was the “fappening” attack (the celebrity nude photos leak in 2014), where multiple celebrities were conned into sharing their iCloud accounts.
...whaling focuses on big targets, such as CEOs, wealthy people, celebrities, or politicians.
SMiShing
Smishing is short for SMS phishing. As you might imagine, it’s the same thing as email phishing but done via SMS texting. These texts can also contain malicious links that install malware when clicked on or convince you to provide sensitive information.
Vishing
Vishing stands for voice phishing. Just like its name suggests, instead of sending fraudulent emails or text messages, the phisher calls the victim, claiming to represent a bank or another authority. From here, the visher uses scare tactics to convince the victim that if personal data or money is not exchanged, they risk facing a substantial punishment.
What to do if you're a victim of a phishing attack
If you’ve been the victim of a phishing attack (or have come close to being one), the steps below will help you mitigate the damages.
Scan your device
If you’ve downloaded something from a suspicious email to your device, it could be infected with malware. If your antivirus software hasn’t warned you about anything, then thoroughly scan your device. If you currently don’t own a reliable antivirus program, then be sure to purchase a full-featured one, such as Bitdefender or McAfee.
Report the attack
The next step is to report the attack to your email provider, impersonated entity (such as a bank), and your country’s anti-fraud commission (the Federal Trade Commission if you live in the US). Reporting a scam helps prevent future attacks.
Freeze your credit
If you’ve given away banking and credit card information, alert your bank as soon as possible. Tell them you’ve been the victim of a phishing scam and want to freeze your account to prevent unauthorized payments. Afterward, check your credit report for any unfamiliar activity in your name.
Change your passwords
If you suspect that malware has been installed onto your device, then be sure to take the following precaution: change the passwords of all of your accounts; create new, complex passwords containing symbols, numbers, and letters; and finally, don’t forget to enable multi-factor authentication for an additional layer of security.
...Create new, complex passwords containing symbols, numbers, and letters.
How to stay safe from phishing
Follow these steps to prevent scammers from coming anywhere near your personal information, including your bank accounts.
Ignore suspicious emails
The best way to avoid becoming the victim of a phishing scam is to ignore suspicious-looking emails. Opening a phishing email is safe, but just be sure that you don’t download an attachment or click on any links — that’s how you wind up getting infected with malware. Once you’ve learned to recognize a scam (by following the above warning signs), you’re a big step closer to keeping your accounts and devices safe.
Don’t click on fishy links
If you happen to open a scam email, always be vigilant about clicking on any links or downloading attachments. If the email contains an urgent task that your bank or some other company requires you to do, don’t click on the links. These will often take you to web pages that will download and install malware onto your device or persuade you to enter your personal information.
...always be vigilant about opening links or downloading attachments.
Never send financial data via email
Banks and online payment sites will never ask you for your personal account details, credit card numbers, or passwords through email. If you encounter such a request, ignore it and contact the bank directly for clarification.
Source: Malwarebytes
Choose a reputable email service
Gmail is the most popular email provider globally, with a user base of over one billion. We recommend it for personal and professional use; still, if you want to use another email service, then opt for a reputable one like Outlook or Yahoo!. There are many email providers out there that may not be as safe and reliable as these services.
Additionally, you could try an email service that’s focused on security, such as ProtonMail, which is protected by Swiss privacy laws.
Source: APWG Phishing Activity Trends Report, Q2 2020
Change passwords regularly
Another way to protect your accounts is to change your passwords regularly. Some banking services force you to do this once in a while, but others don’t. For best results, make changing your passwords a habit. Use strong password generators and make sure to use letters, numbers, and symbols.
Use a reputable antivirus solution
Just about any respectable antivirus solution comes equipped with an email protection feature. However, this option is often only included with premium versions. Check out our comparison guide to help you find the best antivirus solution for all of your needs. We highly recommend a top antivirus solution like Bitdefender or Kaspersky.
FAQs about phishing
What are some examples of phishing?
Phishing attacks can come from email, SMS, instant messaging, or voice calls — the messages you may receive can vary. Attackers will often pose as your bank, boss, colleagues, or friend. Sometimes they’ll even pose as celebrities or well-known brands, etc.
They may ask you for something urgent and provide you with malicious links or attachments. Should you click on these links and attachments, malware may be installed on your device, or you may find yourself on a webpage where you’ll be asked to provide sensitive information.
A trusted anti-phishing program (Norton is a great example) will help you keep phishing scams at bay.
Why is it called phishing?
The word “phishing” was first coined in 1996. It’s similar to the word “fishing” because, technically, they’re similar activities. Hackers cast the bait out onto the internet and wait to catch unsuspecting prey (internet users). The “ph” was added as a nod to an early type of hacking known as Phone Phreaking.
Being vigilant and having a solid antivirus solution can help you avoid the phisher’s net.
Is phishing a type of malware?
No. Phishing is not a form of malware. Phishing refers to the method employed by the attacker to deliver malware. It refers to a victim being tricked into doing something like disclosing sensitive information, clicking on malicious links, or downloading malware.
If you want to stop malware infections through phishing, install a reputable anti-phishing solution.
Can you stop phishing emails from being sent to your device?
Yes. You can stop phishing emails by using a reputable email provider or by purchasing a reliable antivirus program. We strongly recommend Norton for its anti-phishing capabilities.
What happens if I click on a phishing email?
If you’ve clicked on a phishing email, don’t worry. Simply opening an email won’t download or install malware onto your device. That being said, it does increase the likelihood of accidentally clicking on a malicious link or downloading an infected attachment. To avoid this, it’s best to avoid opening phishing emails altogether.
To filter out any potential scam emails from your inbox, use an antivirus program specialized in stopping phishing threats. These applications work to enhance the default email filter of your email provider for great anti-phishing results.
Octav Fedor (Cybersecurity Editor)
Octav is a cybersecurity researcher and writer at AntivirusGuide. When he’s not publishing his honest opinions about security software online, he likes to learn about programming, watch astronomy documentaries, and participate in general knowledge competitions.